 |
Chris Bell | 'A business that makes nothing but money is a poor business.' |
| - Henry Ford |
 |
Chris Bell | 'A business that makes nothing but money is a poor business.' |
| - Henry Ford |
SNHU - IT-600 - Operating Systems
Written by: Chris Bell - December, 2015
Top Secret Inc. is an operating systems company that creates top secret alarm systems for government installations, camera systems for drone aircraft companies and control systems for Fortune 500 companies, but it's struggling to stay updated with technology since they use their own operating system created in-house. Even though TSI is known for their quick response time and highly reliable operation, they still need the latest and great technology to offer their customers. For example, TSI's operating system doesn't support more than one program running at a time or more than one processor on a physical device. TSI also cannot provide a CreateThread() API like Windows or Linux which can severely hurt their chances of getting new customers. Finally, TSI has little security in place and limitations with their software developers that are unable to program ideas for improvement.
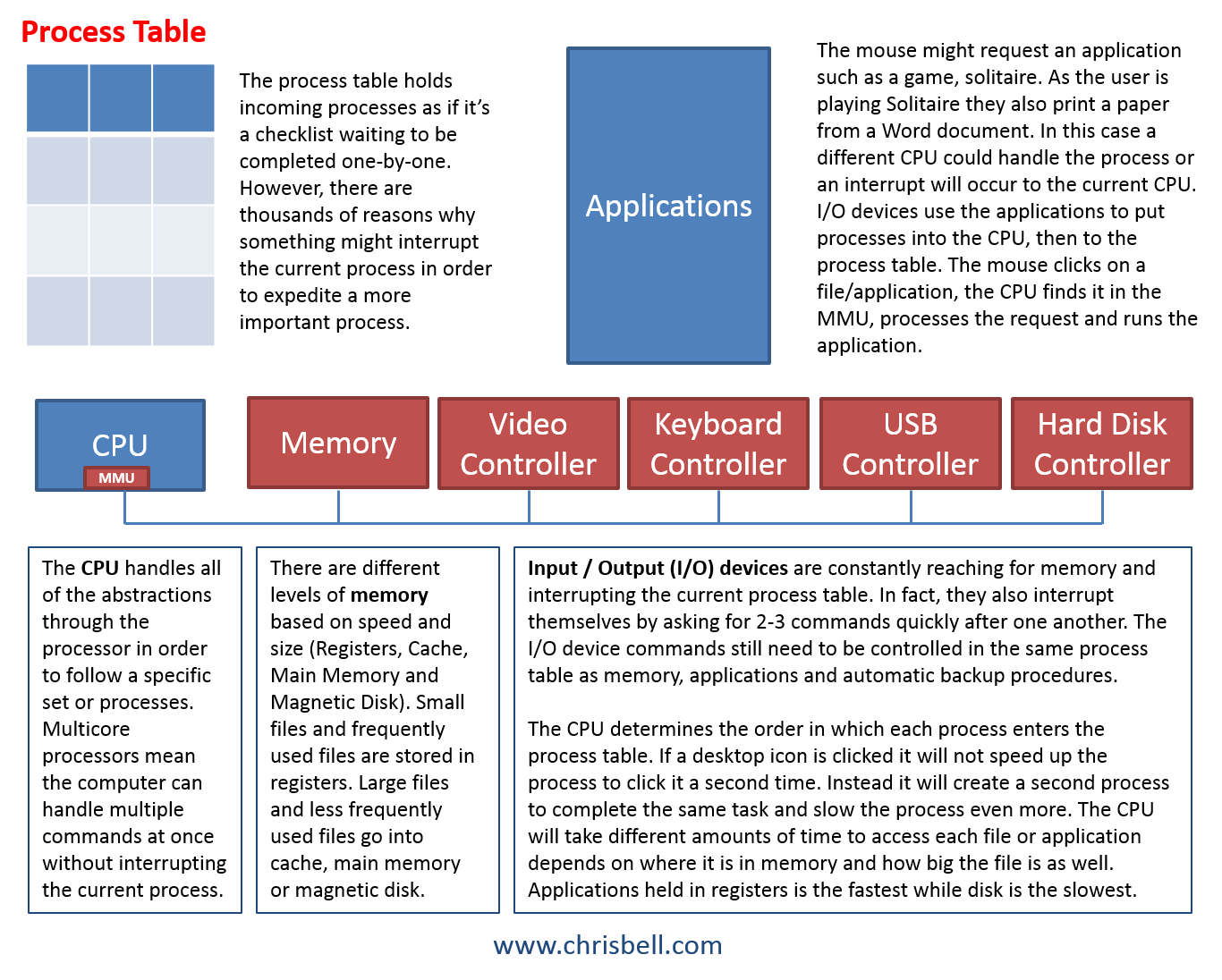
Multiprogramming is an important feature for Fortune 500 companies that may need more than on program running on one processor. To the user, it appears that multiple programs are running at the same time, however, the processor is actually running part of one program and then part of another so quickly that it appears to be simultaneous. As The Crazy Programmer puts it, "Multiprogramming is the ability of an operating system to execute more than one program on a single processor machine. More than one task/program/job/process can reside into the main memory at one point of time. A computer running excel and firefox browser simultaneously is an example of multiprogramming." Since there's only one processor at TSI, interrupts typically cause the operating system to lock up, and they're using old hardware with single-core processors because TSI doesn't support multicore processors. The issues TSI is having wouldn't be as significant if they were dealing with small companies as customers, but they are trying to support government agencies, Fortune 500 companies and the installation of top secret alarm systems. This is probably the main reason that many new software applications are licensed instead of each company trying to reinvent the wheel every time a new application arises.
Multithreading is not something TSI can offer so they use open-source software to remove multithreading functionality which means TSI continues to run in the wrong direction. They are buying old hardware to support single-core processors and using open-source software to limit what their customers can do. Instead, they should be updating technology and moving forward instead of backwards. We'll look into a solution to these problems soon, but for now we're trying to determine the biggest problems and challenges of TSI's future.
Virtual memory and TSI's system call interface create system crashes and compatibility issues. Their customers shouldn't have to worry about the amount of virtual memory they're using, or how TSI needs to modify traps to kernel mode and develop custom system call responses.
Based on the name of the company, Top Secret Inc., one might figure they have a good security system in place, but that's far from the truth. When TSI is working on top secret alarm systems for government installations they should be able to discuss the amount of protection available through security measures, but they can't. As a result anyone that can login to TSI headquarters can also login to any TSI server in the back office.
Device drivers are a big challenge for TSI because their developers write custom device drivers for each customer instead of having a standard format for all customers. This create problems when developers need to make changes and repairs because each customer has different layout, and furthermore, when those developers leave the company it will be difficult for newly hired developers to get acclimated. Similarly, TSI doesn't have a good fault tolerance because the system doesn't recognize problems and fix them unless it's specifically set up with a custom response.
The company I work for, WesBell Electronics, only has 25 employees so I understand trying to save money and competing with much larger companies, however TSI is taking the wrong approach and their customers will soon find out. For example, we can't delivery all of our packages like Walmart, nor do we have developers that can create custom software, so we have UPS and a third party ERP system. A challenge we currently face with our ERP system is that it cannot handle a bill of materials order. If we want to manufacture an item that uses multiple items in our inventory we can put each item on an order and invoice it, however we can't group them together and create a single BOM item (like a recipe of ingredients set as Apple Pie). It would be a great feature for us to have, but it will cost quite a bit of money to upgrade to that type of system, so we haven't done it yet. We are "getting by" just like TSI is using adhesive bandages to fix their problems instead of addressing the bigger problem.
We also hold a lot of personal information from our customers such as names, addresses, credit card information and the companies where they work. We have an IT consultant that handles our security and daily backups. He makes sure our information and our customer's information is protected and secure. TSI needs to work on their security quickly before a big problem arises. Even if it means getting an outside contractor such as an IT consultant to work part time on their security, it could save them from a large data breach.
Since TSI is working with customers of such great caliber they need to work on security measures first. Cisco explains network security as, "your IT partner should explain that network security refers to any activities designed to protect your network. Specifically, these activities protect the usability, reliability, integrity, and safety of your network and data. Effective network security targets a variety of threats and stops them from entering or spreading on your network." Banks are worried about hackers, but they also need to worry about employees stealing and selling information because they have access to most information as well. Once the security is in place TSI can work on the rest of the challenges facing their company one-by-one, and sooner than later.
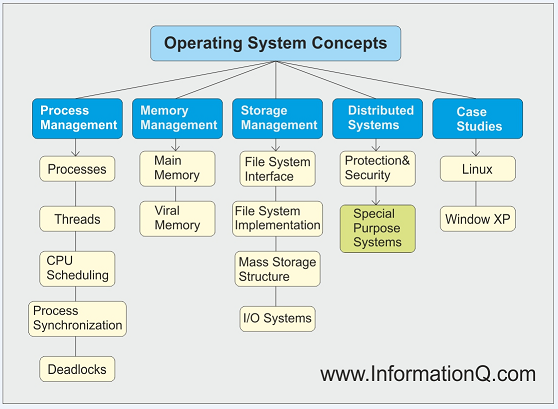
| GPOS Feature | Profile Criteria | Student Analysis |
| Multi-programming | Tech Description | Multiprogramming is the act of parallel processing on a single processor. Programs are not running simultaneously, instead smaller pieces of each program are scheduled until they complete. |
| Business Requirement | Multiprogramming would help TSI because they use a single processor that processes one program at a time similar to First In First Out. If a big program needs to run it would block smaller executions until it completes. If there are 2 bowls of cereal, multiprogramming would eat two bites from each bowl until both bowls are gone, however one person cannot eat from both bowls at the same time. | |
| Application Benefit | Multiprogramming is a benefit because it has a way of appearing as multiprocessing even though it isn't. It's faster when trying to complete multiple processes so more things can be done in a single day. | |
| Implementation Tasks | Implementing multiprogramming involves creating the program on the operating system that completes tasks in the order in which the programmer sets. For instance, it could be set to complete the x amount of bytes of each program in the process table until finished. | |
| Multi-processing | Tech Description | Multiprocessing is different from multiprogramming because there are multiple processors that can in fact work on two processes simultaneously. Multiprocessor, multicore, dual processor and two human brains all describe multiprocessing well. Processes are bigger in size than threads and need to access memory to complete. |
| Business Requirement | This would be the upgrade of a lifetime for TSI because speeds would double compared to a single processor system. Imagine giving a busy human a second brain to double their output in order to imagine how helpful multiprocessing would be as an upgrade. | |
| Application Benefit | Multiprocessing benefits any system that currently only has one processor. It's much faster than multiprogramming on one processor, but multiprogramming still exists on multiple processors as well. It's faster and more efficient. | |
| Implementation Tasks | Implementing multiprocessing would involve another CPU, or processor to be installed. Then the operating system would have to be programmed to use both processors for the best and most efficient use. | |
| Multi-threading | Tech Description | Multithreading is shared in cache to be accessed much quicker (either through cache or registers). Threads are smaller and create a process together. Threads, processes and programs are all under a similar roof by stating, smaller is faster and bigger is slower. Processes need to access main memory which takes longer, while threads are more scalable due to their quick processing in RAM. |
| Business Requirement | TSI is currently removing threading functionality through open source software because they lack a system call interface beyond open, close, read and write. TSI can't create multiple threads. | |
| Application Benefit | Threads are quick access so multithreading is faster than multiprocessing. However, multithreading can make multiprocessing faster because threads make up a process in the process table. | |
| Implementation Tasks | TSI needs a better system call interface that supports more commands and multithreading. Their system will be more efficient and easier to use long term. | |
| Virtual Memory | Tech Description | Pages of data transfer from RAM to disk to avoid system crashes. It's a temporary transfer when RAM becomes overloaded. I can use my brain for quick access to my memory, but if I need to remember 10 things I should write them down to avoid my brain from crashing. |
| Business Requirement | TSI has insufficient memory and their system constantly crashes forcing the administrators to reboot the system. They need a virtual memory model that using paging to avoid system crashes in the future. | |
| Application Benefit | First of all, the system will crash much less often. Virtual memory would stop programs from running into each other when the threads have their own address space. | |
| Implementation Tasks | It would be hard for TSI to implement on their own, but it would be done by giving the threads their own address space to be retrieved in cache. Then allow multiple programs to use the threads at the same time. | |
| System Call Interface | Tech Description | The system call interface sits between the user's application and the kernel. Every time the user clicks, types or tries to command the computer to do something, the system call interface translates that into kernel language to execute the command. TSI needs to develop custom "kernel language" for each customer along with manually repairing problems. |
| Business Requirement | TSI creates custom system calls because they only have a basic interface that isn't compatible with other types of software. There's a lot of manual labor for the developers to repair and maintain current software, and to get new customers. For instance, if one of TSI's customers downloaded Microsoft Word the developers would have to create a special call to use it. | |
| Application Benefit | A better system call interface would benefit TSI from creating work-arounds for current customers. Their systems would be more fluid and easier to implement in the first place. | |
| Implementation Tasks | Perhaps TSI can go through a laundry list of tasks to implement their own system call interface. All of the standard things people need to "system call" programs from the operating system should be created as a template for their operating system software. | |
| Security | Tech Description | Security protects software from hackers, or anyone without authorized access to the system's information. Aside from hackers, it's also important to make sure employees only have access to necessary portions of the system or there's a risk of an employee stealing data to sell it or use it. |
| Business Requirement | TSI has a frighteningly low amount of security without protection for log in, file system modifications or network. Therefore, anyone can log in to manipulate files which doesn't make much sense for a company that's in business creating OS software. | |
| Application Benefit | Security is a priceless thing to have and the benefits would be endless. TSI could get more customers based on promoting better security, but they lack in that area. | |
| Implementation Tasks | They could even use an outside source for security because it would be better than what they currently have. Security is like training because every line of code helps. TSI could start by only allowing access of the system to certain job descriptions. | |
| Device Drivers | Tech Description | Within its name, a device driver controls the connection of a device to the program. A software disk installed for a printer would be considered a device driver. |
| Business Requirement | TSI writes their own custom device drivers because their OS doesn't play well with others. TSI developers have to create different device drivers for each customer because they each use different devices and need custom programming to make them work. | |
| Application Benefit | TSI would benefit from having better compatibility with device drivers, however it's not the most important thing for them to work on when their operating system lacks other key components. | |
| Implementation Tasks | TSI would have to create software to allow other device drivers to function on their operating system. Then they won't have to program every new device driver for their customers. | |
| Fault Tolerance | Tech Description | Fault tolerance tolerates problems and prevents the system from crashing. If the system has crashed for the same reason it's possible to create a program that makes a change before the crash happens. |
| Business Requirement | TSI develops their own device drivers but they have trouble programming everything that they'd like to create due to lack of programming skills. They need to pay for additional fault tolerance by hiring a more experienced programmer. | |
| Application Benefit | A new programmer could help TSI prevent the system from crashing as often as it is now. They could retain more clients and use it to promote the operating system to new clients. | |
| Implementation Tasks | A more experienced programmer would implement programing code that doesn't allow the system to crash as often. | |
| Multiprocessing and multiprogramming on each processor is necessary for TSI to upgrade their operating system to handle. Upgrading to virtual memory and increasing security are also two big concerns of the current system because TSI will need to discuss those topics with customers. We would plan to outsource security options, hire new programmers to implement virtual memory and multiprogramming. TSI still wants to handle everything in house so we'll accommodate them with more experienced staff. | ||
Deadlock avoidance is important for TSI to configure so that their server can operate 24 hours per day, and so that customers can always access the website to make purchases during peak periods. Deadlocks happen when servers are busy processing multiple programs at the same time and when certain programs request the same threads. For example, two production employees start Job A and Job B that both require Tool 1 and Tool 2. Job A gets a hold of Tool 1 and requests Tool 2, however Job B already got a hold of Tool 2 and requests Tool 1. Both Job A and Job B are now in wait mode for another tool in which neither of them can get. That analogy relates to processes requesting threads to complete the entire process. Sometimes processes need the same threads that are never going to be available because neither process has all of the required threads to execute.
Luckily, there are algorithms that avoid deadlocks by initially waiting for all of the threads to be available before beginning the process. For example, Job A above wouldn't have grabbed Tool 1 until all of the necessary tools and parts were available, then it would grab all of them together. Another way to avoid the deadlock would be to grab the tools and parts one-by-one, but release them back if a duration of time has gone by. Perhaps Job A has held 3 of 4 tools needed for the job for 10 minutes, so the algorithm can now release them back to the shelf before the deadlock occurs. There are a few ways to solve the problem but some of the solutions create new problems as well.
Waiting for every necessary thread to be available before locking them in the mutex can be problematic because the amount of time is unknown and could actually be infinite. There might be one of five threads always being used by another process and never actually have all five available at the same time. As threads enter the mutex they are locked (pthread_mutex_lock()) and when they exit the mutex they are unlocked (pthread_mutex_unlock()). Once a thread is locked into a mutex it cannot be used elsewhere creating the opportunity for deadlocks. However, if the currently locked threads are in the mutex knowing that all threads are available then the process will finish, unlock, and make those threads available to other processes that need to be executed.
Holding and locking threads one-by-one for a predetermined amount of time will stop the deadlock from happening because those threads will be released if the rest aren't available and locked within that time period. Then the process of locking the needed threads can start over. QNX, a subsidiary of Black Berry says, "Only one thread may have the mutex locked at any given time. Threads attempting to lock an already locked mutex will block until the thread that owns the mutex unlocks it. When the thread unlocks the mutex, the highest-priority thread waiting to lock the mutex will unblock and become the new owner of the mutex. In this way, threads will sequence through a critical region in priority-order."
With the Hold and Wait deadlock avoidance in place, in the introduction example, Job A would have held Tool 1 and waited for Tool 2. Since Job B was already holding Tool 2 and requesting Tool 1 they would have gotten it to complete their job. Then Job A would request and hold all of their tools again until all of them are available.
References:www.cisco.com (n.d.). What is Network Security?Retrieved from: http://www.cisco.com/cisco/web/solutions/small_business/ www.thecrazyprogrammer.com (Dec, 2014). Difference Between Multiprogramming, Multitasking, Multiprocessing and Multithreading. Retrieved from: http://www.thecrazyprogrammer.com/2014/12/ No Author (n.d.). Methods for Handling Deadlocks Retrieved from: http://www.gitam.edu/eresource/comp/gvr(os)/7.3.htm No Author (n.d.). pthread_mutex_lock(3): Linux Man Page Retrieved from: http://linux.die.net/man/3/pthread_mutex_lock Tanenbaum, Andrew S. & Bos, Herbert (2015). Modern Operating Systems, Fourth Edition. Upper Saddle River, NJ: Pearson Education, Inc. |